The last post, Transformational Cyber Security Part I, discussed exciting inventions that turn cybersecurity upside-down by preventing malware from freeloading CPU instructions in a properly configured software defined data center (SDDC), thereby rendering on-premise cyber attacks null and void. It also discussed root-of-trust encrypted metavisor technology that protects applications and data operating in the cloud.
Now, the cyber vulnerability challenge becomes adopting these technologies into the massive global IT infrastructure, faster than cyber attacks can debilitate significant elements of our world. This post introduces additional cyber technologies to enable protection against cyber intrusion between customer offices and the cloud. It includes secure cloud data and distributed ledger technologies to protect all transaction activities that intersect with the cloud.
But first it is useful to consider who is responsible for information protection as commercial cloud offerings continue to grow. The IT world is in the middle of a paradigm shift from private data centers, to combinations of private and commercial cloud services that offer the promise of reducing or eliminating IT staffs in favor of IT services delivered to us users anytime, anyplace, and worry-free. This model is similar to the way we enjoy worry-fr ee electric power; at least most of the time.
ee electric power; at least most of the time.
While first world countries have come to trust that the commercial electricity service and the electric grid moving it are very reliable, many homes, most large businesses, and all of the world’s data centers use backup electric generators to reduce or eliminate crippling losses of electric power. Just as the world cannot long survive without electricity, it now cannot survive without information flow. Consider, for example, that all of civilization’s necessities are now controlled by information systems and processes that enable efficient food flow, water flow, money flow, energy flow, and information flow itself, where 95% of all telco information transits undersea fiber optic cables.
 Like electricity, information must be protected from mishandling, data-theft, data alteration, and data-flow interruptions. In this respect, cloud providers do a good job of engineering security into their cloud systems, and provide independent verification of compliance certifications such as HIPPA to protect health records, ISO 27018 to protect personally identifiable information (PII), and Cloud Security Alliance (CSA), to help cloud customers assess how cloud service providers follow and comply with industry best practices, standards, and regulations.
Like electricity, information must be protected from mishandling, data-theft, data alteration, and data-flow interruptions. In this respect, cloud providers do a good job of engineering security into their cloud systems, and provide independent verification of compliance certifications such as HIPPA to protect health records, ISO 27018 to protect personally identifiable information (PII), and Cloud Security Alliance (CSA), to help cloud customers assess how cloud service providers follow and comply with industry best practices, standards, and regulations.
Commercial cloud services have opened amazingly positive low barrier of entry opportunities for new-start companies, plus medium and large businesses alike, but they cannot fully solve the challenge of data liability, which must continue to be the customers responsibility. That responsibility forces all customers to self-protect and backup all sensitive data, including PII, financial, intellectual property, private applications, and company process information. To do so, cloud customers must be augmented by some form of extra-cloud protection, or use a hybrid private/commercial cloud architecture, similar to the way we use backup generators for our critical electricity needs. We know this because even with cloud providers doing their best to support the protection of customer data, as daily news reports attest, cyber attacks, like ransomware, continues to plague the world.
By protecting the telco connections from a customer to the cloud and then extending additional cybersecurity technologies further up the IT stack, commercial cloud-only, or hybrid-cloud architectures will start to deliver high-reliability cyber protection to cloud users and the clouds they ride. One company* now offers a Software Defined Perimeter (SDP) service that transparently authenticates each user device, followed by authenticating the user and the data center or cloud application that the user is accessing. In this way the SDP is creating a private network enclave similar to the way the DoD divides users across different security enclaves in order to protect classified data. If desired, this SDP can be established with a dedicated network path all the way back to a telco provider.
Another company** has invented a database technology that is capable of searching encrypted data without holding the encryption keys to that data. The implications of this semi-homomorphic encryption invention is massive. It enables the creation of a zero-trust trust data-layer, thereby eliminating the data-layer cyber threat surface, where data spends 99+% of it’s time. This allows cybersecurity to spend cyber resources focused on the small remaining cyber threat surface.
With this revolutionary data-layer technology, this same company** discovered they could leverage the secure data-layer to create secure immutable distributed ledgers that protect and verify all transaction processes. Secure distributed ledgers is the goal and the hype behind blockchain technology, first introduced by the inventors of the Bitcoin cryptocurrency. Immutable distributed ledgers are desired because they are not vulnerable to a central data location, they cannot be altered without the string of block participants agreeing to the change, and they are transparent for authorized audits without fear of illegal ledger modification. The importance of this company’s technology is that it secures the distributed ledger transaction blocks in zero-trust layers and is massively scalable, unlike the challenge with current blockchain ledgers.
The last company*** in this cyber secure stack is a company that has created a secure distributed artificial intelligence (AI) technology that distributes smart-agents anywhere within an information processing echo-system, like supply-chains, industrial processes, and AI augmented human control processes such as military command and control. These AI agents operate within a common software support platform and are assigned behaviors using a library of behaviors tailored to the needed automated task.
By increasing the security at each layer of this IT infrastructure stack, as shown in this diagram, cybersecurity is now moved from a high risk profile, hoping that ransomware and other malware will not disrupt operations, to a highly security and reliable IT system, equivalent to military grade cybersecurity.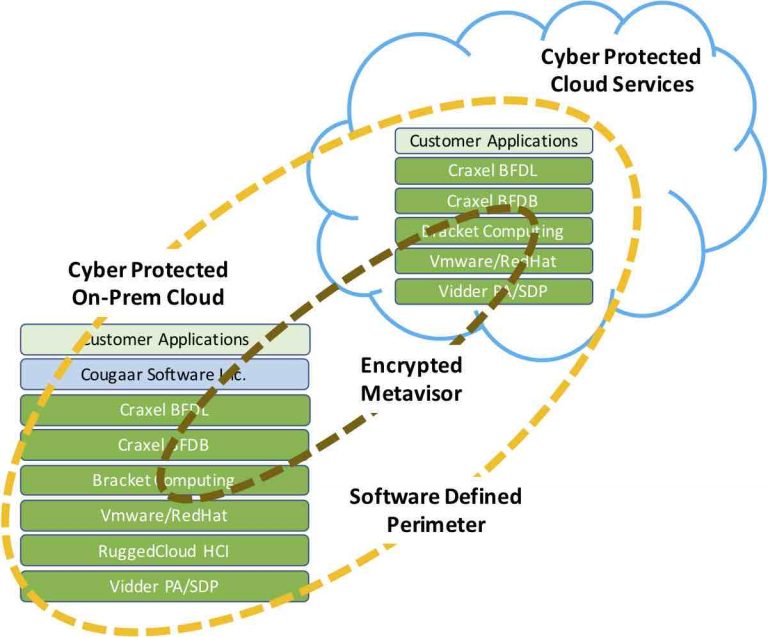
As the world continues accelerating into the AI future of autonomous car and truck transportation, 3D printing that is revolutionizing manufacturing, and robotics promising Star Wars like helpers, the big elephant in the room is cyber vulnerability. Without solving this challenge, not only will our National infrastructure continue to be at risk, but our software driven government and businesses processes will be unable to adequately compete in this new global landscape!
*www.vidder.com* **www.craxel.com ***www.cougaarsoftware.com









