Cyberspace is our interconnected information technology. And since everything either is or is becoming connected, one of the defining characteristics of cyberspace is its complexity. This adds burden to cyber defenders. Defense teams require experience, education, training and a mindset that lets them continually learn. They also must forge broad teams across multiple subject and functional areas. An ability to rapidly collaborate and exchange data while in a fight is a must.
For years computer security professionals have sought the best ways to dialog on incidents, and some great foundational work has been done in this area. This post reviews a work found to be of special relevance to today’s cyber defenders, a 1998 publication titled “A Common Language for Computer Security Incidents.” This foundational work is important since it is a bit of a stage setter relevant to all the current work I see on standards for information exchange and even human dialog/discussion.
What is a taxonomy?
A taxonomy is a set of related terms. It is a classification scheme. How do you judge a good taxonomy? It should meet several criteria, including being:
- Mutually exclusive – classifying in one category excludes all others because categories do not overlap,
- Exhaustive – taken together, the categories include all possibilities,
- Unambiguous – clear and precise so that classification is not uncertain, regardless of who is classifying,
- Repeatable – repeated applications result in the same classification, regardless of who is classifying,
- Accepted – logical and intuitive so that categories could become generally approved,
- Useful – could be used to gain insight into the field of inquiry
Caution: there is probably no such thing as a perfect taxonomy. They are all approximations of reality and therefore you will never have one that meets every criteria perfectly. But the characteristics above are good goals to judge the taxonomy by.
When it comes to cyberspace activity, the taxonomy presented by John Howard and Thomas Longstaff comes pretty close to meeting those goals which is why it is still so relevant today.
They define a taxonomy of terms in a way that can be logically and graphically expressed.
See, for example, the picture below:
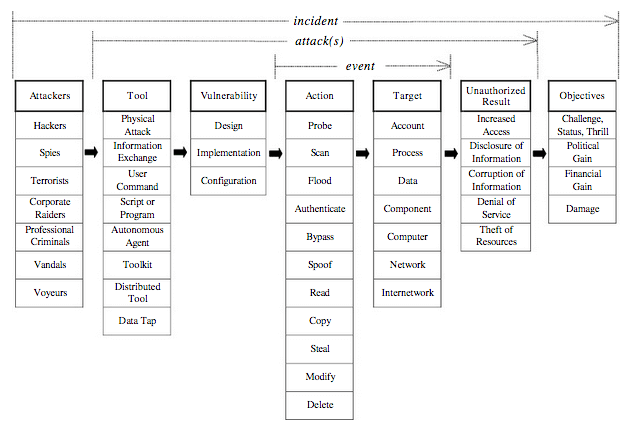
This is from their report and it lets you related terms in a way that can help in dialog between humans and also help in automating information exchange.
The top line of words can be easily thought of as a sentence. Attackers use Tools against Vulnerabilities to cause an Action against a Target to achieve an Unauthorized Result to meet an Objective.
The details of their work spell out with clarify what the individual terms are and that is also a huge help to dialog. Over time there has been a little modification by operational users on some of the terms, and the adversaries in cyberspace have continued to change their craft and a few more terms have entered the lexicon. But overall the framework is sound.
Since this first ground-breaking work the community has continued to improve on this notion, converting concepts into processes and standards and influencing the technology used in cyber defense. Some of the greatest work in this domain is coordinated by MITRE. I’ll make that a topic for future posts, but for an overview of their current work see: MITRE Cybersecurity Standards and especially the MITRE ATT&CK Framework. Modern defenders benefit greatly from these approaches. As you dive deeper into modern standards and frameworks for cybersecurity, keep in mind how it all began, with a great taxonomy from John Howard and Thomas Longstaff published in 1998.
More Reading:
- Awake Yet? The list of cyber security wake up calls grows as predicted
- How do you define cyberspace?
- CTO-as-a-Service: When your enterprise needs deep technical expertise on demand
- Cybersecurity and IT standards and standard bodies
For more on these topics see the CTOvision Guide to National Security Technology and