RiskIQ’s PassiveTotal leverages the power of a well engineered sensor network and high power/high performance computing, and highly experienced analysts to help enterprise executives proactively block or otherwise disrupt malicious infrastructure.
PassiveTotal is designed to provide analysts with a single view into all the data they need. It is also designed to be easy to use. This post does a fast walk through aimed to underscore how quickly you can get from login to actionable results.
Step One: Join for free and log into PassiveTotal.org
Step Two: Click on the “Learn” menu item. For me the mark of a good solution is one where you can dive as deep as you want into all the features of a capability with little or no assistance. This page lets you do just that. One concept I recommend you review on this site is the concept of passive DNS. This source of information is very useful to analysts and researchers seeking to learn about other participants in the Internet, and the succinct overview here provides a great primer for those new to the concept.
Step Three: Return to the main PassiveTotal.org page by clicking on the Passive Total logo. You will see a simple search box at the top of the screen. Enter any domain you want to research into there. To see how this can benefit you when you are researching domains you know little about, try researching one you believe is compromised. A quick and easy way to do that is find some from your spam folder. I just saw a spam that encouraged me to visit a domain called 2homework dot com. I entered that in the search.
Here is the first thing PassiveTotal.org showed me on this domain:
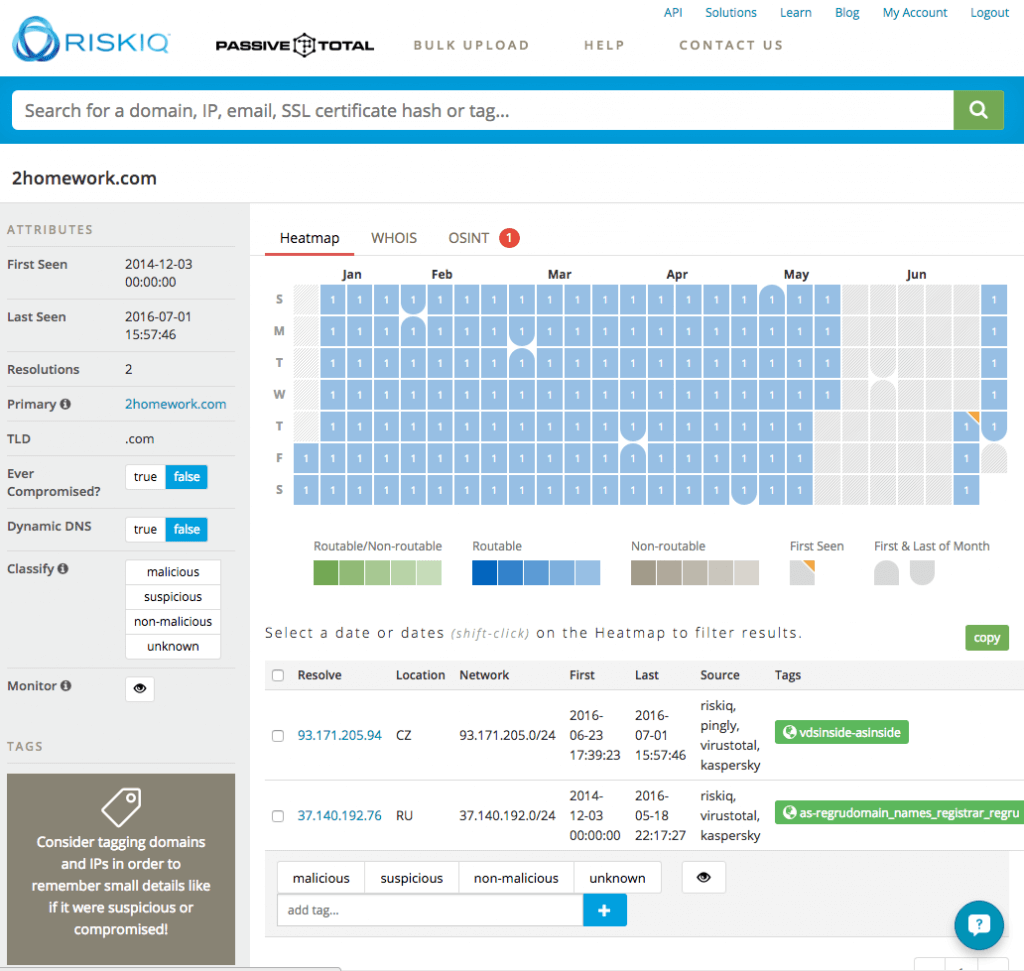
This instantly reveals some key information. One, on the heatmap, it is clear that there is not a lot of DNS activity around this domain. There is data in the PassiveDNS data set and records can be viewed by clicking on any date. But it is interesting that there was a break in the ability to route to this DNS. The reason why is explained below. Registration of the domain switched from a Russian site to a Czech network. We can also see at the top of the heatmap that we can click tabs to see more info from whois and OSINT. There is a bright read dot next to the OSINT tab making me want to check that out first.
Clicking that tab reveals the following:
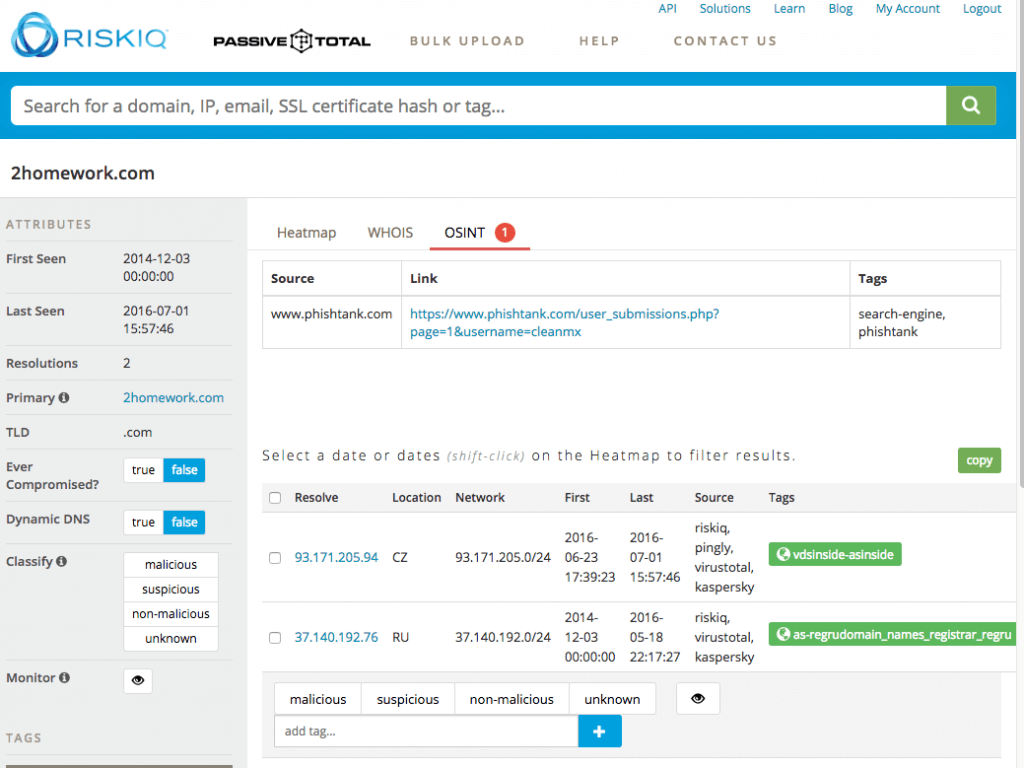
We should also examine the Whois Tab:
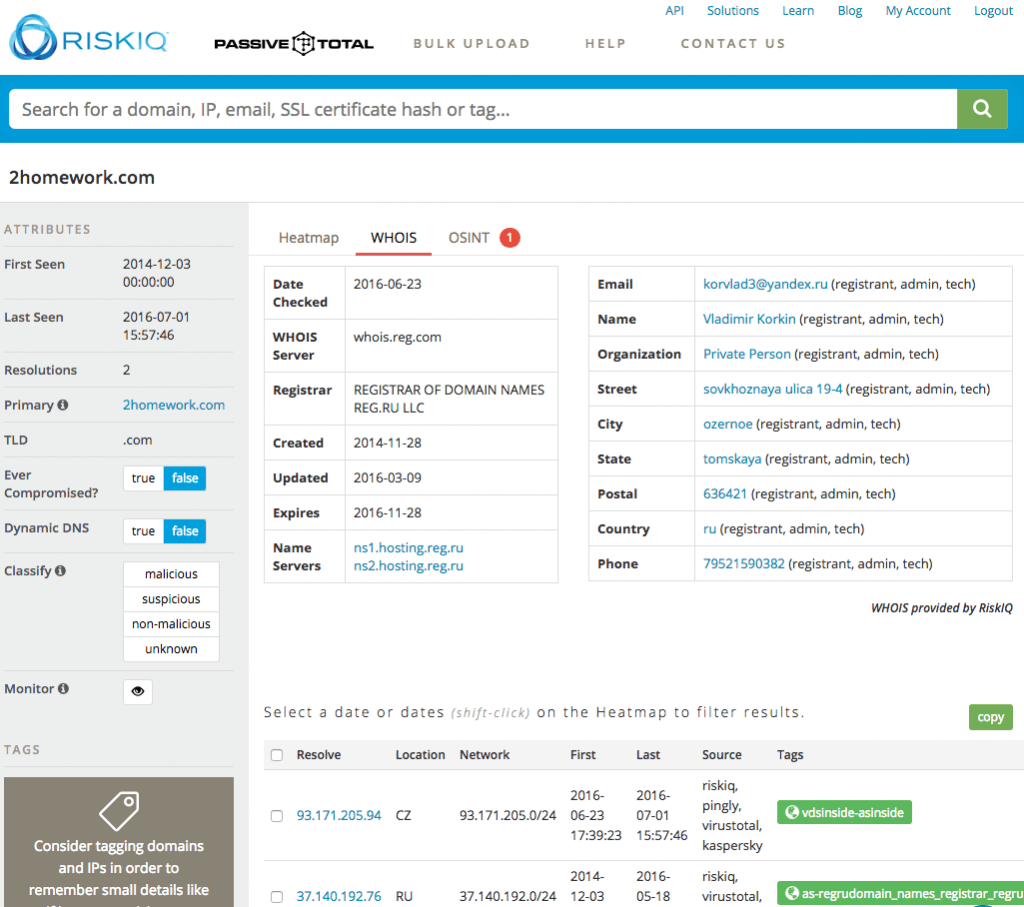
This approach to Whois is very powerful since you can easily click on any key info and learn more from additional data sources on the entities, organizations and locations referenced. For example, clicking on the Name shows that many other suspect sites are registered by the person of interest.
This is one of the more simple but fast and powerful use cases. Now imagine what you can do when you leverage the data that is included on every known malicious entity on the net, including what their attack histories and methods are. And think of how you can track the bad guys in context of your own exposure on the Internet. We have really just waded into the very powerful capabilities of PassiveTotal. Explore it your self at: https://passivetotal.org
To learn more see the CTOvision Solutions Directory: RiskIQ
Related Reading:
Social Media: Change, Control and Security
Moving Your Decision Science Team from Reactive to Proactive
Main Street Cybersecurity: Can Email Be Safe?
This One Little Configuration Change Will Make It Harder For People To Steal Your Information