The FFIEC (Federal Financial Institutions Examination Council) is a formal interagency body empowered to prescribe uniform principles, standards, and report forms for the federal examination of financial institutions by the Board of Governors of the Federal Reserve System (FRB), the Federal Deposit Insurance Corporation (FDIC), the National Credit Union Administration (NCUA), the Office of the Comptroller of the Currency (OCC), and the Consumer Financial Protection Bureau (CFPB), and to make recommendations to promote uniformity in the supervision of financial institutions. In 2006, the State Liaison Committee (SLC) was added to the Council as a voting member. The SLC includes representatives from the Conference of State Bank Supervisors (CSBS), the American Council of State Savings Supervisors (ACSSS), and the National Association of State Credit Union Supervisors (NASCUS).
For the last several years the FFIEC has been making contributions to cybersecurity awareness, including initiatives aimed at helping financial institutions better understand and deal with cybersecurity risks. In June 2013, the FFIEC announced the creation of the Cybersecurity and Critical Infrastructure Working Group to enhance communication among the FFIEC member agencies and build on existing efforts to strengthen the activities of other interagency and private sector groups. In addition, the FFIEC began assessing and enhancing the state of the industry preparedness and identifying gaps in the regulators’ examination procedures and training that can be closed to strengthen the oversight of cybersecurity readiness.
On 30 June 2015 the FFIEC released a new Cybersecurity Assessment Tool. This tool is intended to help financial organizations large and small better assess and understand risk and also the organization’s maturity in cyber defense.
We have worked with financial institutions and other high risk organization in cyber security assessments for years and have seen first-hand the benefits that the FFIEC approach can provide to organizations. We have also captured many lessons learned from our engagements across the financial (and other) sectors regarding this approach. We share some of those lessons here:
- The most important lesson is to understand that the FFIEC CAT should not be seen as just a compliance drill. Regulators will check you for compliance and that is very important. But if used correctly it can also help an organization become more efficient, effective and more secure.
- The tool is meant to help and is not designed to be a one-size-fits-all approach. It is best when tailored to your specific organization.
- The most important determinant of whether or not the tool will work for you is the attention it gets from senior leadership. And getting their attention means approaching it with the vision of leveraging it to support and enhance business functions. In the financial industry that usually means focusing on enhancing trust among customers and partners.
Here are more thoughts:
The tool has two parts. The first assesses the institution’s inherent risk profile based on five categories:
- Technologies and Connection Types
- Delivery Channels
- Online/Mobile Products and Technology Services
- Organizational Characteristics
- External Threats
It is this first section that is the most problematic. It seeks to quantify cyber risks in a very simple way, and this is actually a very complex and hard to measure/quantify topic. On top of that, the best topics to address regarding risk are going to vary significantly from company to company, and even division by division for larger firms. Perhaps this first section can just be thought of as a rough plan to deviate from. It can be an important drill to seek to assess cyber risks, of course, but it seems both arrogant and naive of the FFIEC to think that they can produce a matrix that captures risk for every organization. Since most organizations in the highly regulated financial sector will already have a chief risk officer and many risk processes around cyber, maybe this section should just be offered as a template of considerations.
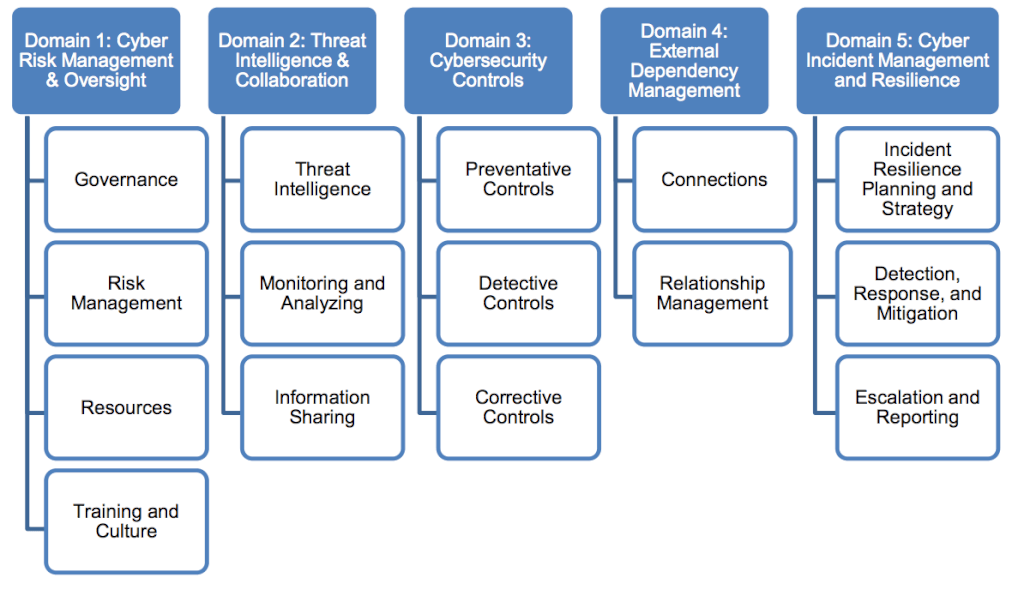
The second section of this tool brings some good ideas and approaches to evaluation of the organization’s Cybersecurity Maturity five domains:
- Cyber Risk Management and Oversight
- Threat Intelligence and Collaboration
- Cybersecurity Controls
- External Dependency Management
- Cyber Incident Management and Resilience
This is were the tool can make contributions to many organizations. The descriptions and definitions for each of these domains and then the assessment factors in each domain are useful, especially for organizations that do not already have an approach to cybersecurity.