This is the first in a series of blog posts examining a cloud-based enterprise. In this post we’ll introduce how a Secure Enclave can help enterprises migrate to a cloud-based model.
The two dominant themes in enterprise architecture today is the desire to save money by utilizing cloud services and threat of state-sponsored cyberattacks. The goal of a Secure Enclave is to help enterprises meet both objectives by implementing a trusted access control solution in the cloud.
All IaaS and SaaS providers utilize a shared security model in which they take responsibility for the data inside their boundary but expect the enterprise to be responsible for everything outside their perimeter. For example, enterprises are responsible for all damage due to stolen passwords or unauthorized access to compute instances. Thus the security challenge for cloud-based enterprises to how to enable perimeter security when all they have is the cloud?
A Secure Enclave utilizes a Software Defined Perimeter (SDP) security model to create a protected IaaS instance inside which role-based access control, trust assessment, certificate management and addressing functions can be deployed. Additionally a Secure Enclave can also protect IaaS and SaaS applications from network-based cyberattacks including self-propagating malware.
Looking at the high level architecture below we see Secure Enclaves supporting trusted access control functions for IaaS and SaaS applications.
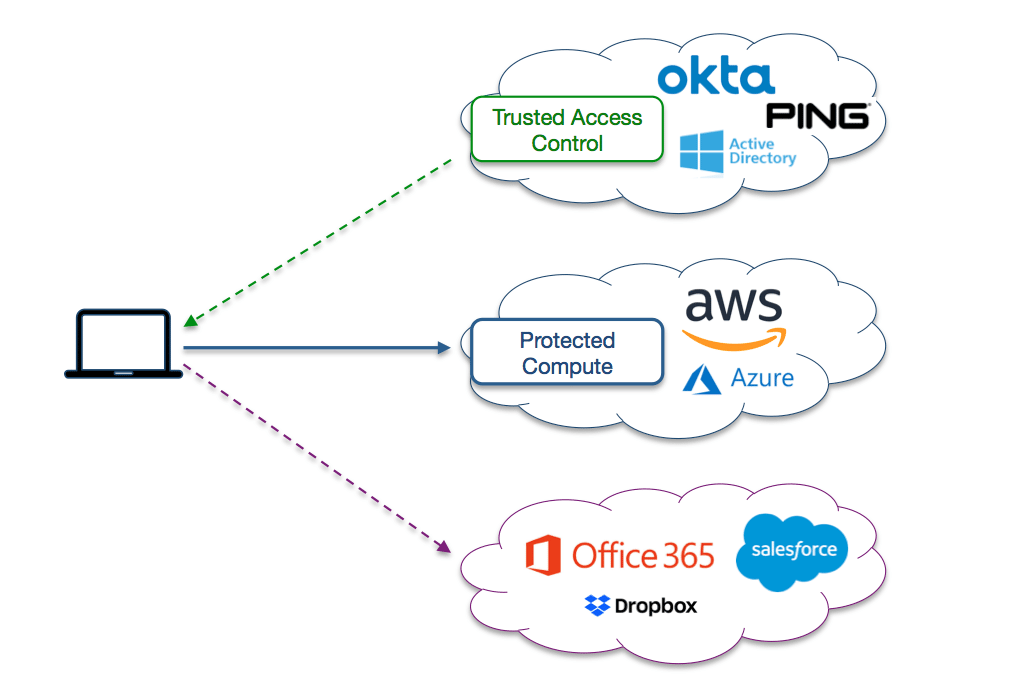
The first task of a Secure Enclave is to implement trusted access control to IaaS and SaaS applications. Trusted access control combines role-based access control with device trust assessment. Trust assessment allows enterprises to conduct a remote posture check on user devices before granting access to cloud services. For example, enterprises can verify if a device has updated software and is running endpoint protection. If the device is acceptable then one or more SAML assertions are generated based on the role of the individual.
Secure Enclaves can also be used protect IaaS instances from network-based cyberattacks. Only authorized users and their devices are granted TCP connectivity to IaaS compute instances. Moreover to block the new generation of self-propagating malware, only application layer connectivity is granted to authorized devices.
One of the unique features of a Secure Enclave is how it protects SaaS applications from stolen passwords. Enterprises can utilize the federation capabilities to SaaS apps to re-direct sign-in requests to their SAML IdP. However only users who have access to the protected IdP can get the SAML assertion. Thus Secure Enclaves can be used to provide transparent multi-factor authentication to SaaS.
In the next post we’ll take a deeper look at the trusted access control functions of the Secure Enclave.