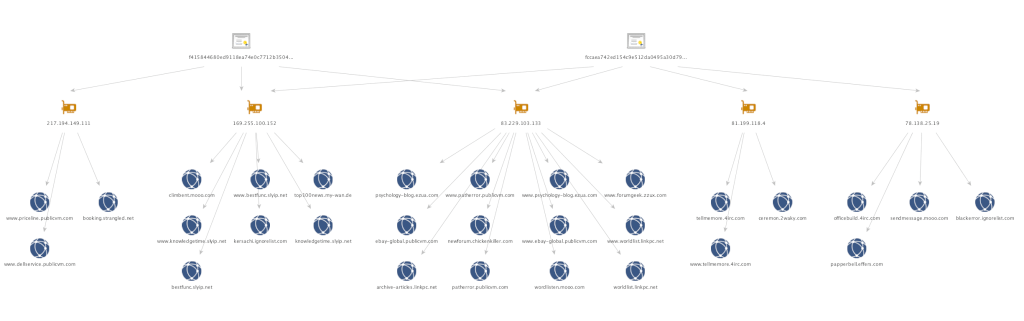
For the last year Passive Total has been providing open analysis on an interesting piece of adversary infrastructure and in doing so are shedding informative light not just on that particular adversary activity but on how multiple sources of information can be pulled together to form a more complete picture of what is going on. For example, by understanding the relationships between datasets including open source intelligence, historical DNS records, known malicious domains, historical SSL certificates and numerous facets within those and other datasets, a more comprehensive understanding of an adversaries attack infrastructure can be built out. PassiveTotal is a clear master of this approach to “Infrastructure Chaining” for analysis.
In February PassiveTotal provided an update on research into a known adversary campaign that has been reported by Kaspersky as APT Command and Control in the Sky. Commonality with other intrusion sets resulted in this being associated with a group many analysts believe is Russian, but as you can imagine it is hard to find the smoking gun. One of the more interesting elements of this set the way malicious code command and control is being conducted via compromised satellites. Sounds expensive doesn’t it? Well it is not expensive. Attack probably cost the adversaries about $1000.00 in hardware plus engineering time.
In the February update, PassiveTotal showed how they could kick off an analysis armed just with Kaspersky’s open source intelligence report, then dive deep into their datasets on known adversary infrastructure, historical DNS records and current and historical security certificates, and then combine that to produce new knowledge and insights. Their reporting make it clear that this adversary had been operating in this way since at least 2013, and was also penetrating many other adjacent targets. Turla could be shown to have compromised an extensive network of satellite providers and was leveraging a large network of command and control servers as part of this operation.
Perhaps more interesting was an update in August 2016 where PassiveTotal revealed that before publishing their report they set up alerts in their datasets to see if their report would cause any action by the adversary. Smooth move there PassiveTotal, that is great tradecraft. It was interesting to see that yes the adversary did adapt and could be traced as they did. PassiveTotal could watch as an entirely new infrastructure was brought online. They then manually followed and assessed compromised IP addresses and continued to correlate and link across multiple datasets to flesh out what the new adversary infrastructure looked like.
For more see: Snakes in the Satellites: On-going Turla Infrastructure
For more see: