 From the 1930s to 1950s (far too long) the medical community just would not wake up to the fact that cigarettes could cause harm (see More Doctors Smoke Camels). Why did they stick with this misperception for so long? When so many good people come to the wrong conclusion it probably means some deeply human cognitive biases are at play. Most people have a long studied desire to prefer the status quo. If this is what was always thought, why think differently?
From the 1930s to 1950s (far too long) the medical community just would not wake up to the fact that cigarettes could cause harm (see More Doctors Smoke Camels). Why did they stick with this misperception for so long? When so many good people come to the wrong conclusion it probably means some deeply human cognitive biases are at play. Most people have a long studied desire to prefer the status quo. If this is what was always thought, why think differently?
They are not the only groups of humans to stay anchored to old ways. For years nutritionists believed that all calories in food are the same, including all forms of sugar. This led to the conclusion that we might want to watch calories overall but sugar is great. Now that obesity is an epidemic and diabetes the fastest growing disease in the world, most professionals realize that too much sugar is bad. But even after it was discovered that Harvard medical researchers were paid to lie in studies about sugar, humanity is still almost totally ignoring this topic. Clearly there are cognitive bias issues here too.
The technology community is not immune to getting stuck with an opinion and not wanting to shift, even in the face of evidence. One of the big ones is that you need to use a personal VPN.
In 2010 it was good advice to recommend a VPN for personal use. But in my view, any technologist or security professional recommending that now should be ashamed for not keeping up with the enormous changes in technology over the last decade.
The rest of this post will dive a little deeper into the topic.
To summarize up front: For almost every use case, the only reason to use a VPN is if you are using one provided by a business that requires you to use it to access corporate resources. Some also use VPNs so they can access content that is restricted by geography. You do not need a VPN for your home or small business use, even when using public WiFi. Personal VPNs just don’t add value to your security posture.
What Some Of The Experts Saying About VPNs:
A sponsored piece at CNN says “A VPN is vital when working from home“. This piece, written in the form of a CNN article but apparently paid for by a VPN provider, claims that data that flows from your computer to the Internet is open and accessible to anyone who can intercept it (this statement is false). They also say that without a VPN, anyone with the right tools can intercept passwords, banking information and everything else you transmit (this is also a false statement).
CNET tells us that “Anyone who wants to protect their privacy and security online should use a VPN.” This myth is all over the place, especially on sites where companies that provide personal VPN services advertise.
Gizmodo asserts that: “The benefits of virtual private networks, or VPNs, are well-documented: They keep you safer on public wi-fi ” This may have been true in 2010, but the technology of the Internet changed when Gizmodo wasn’t watching.
Norton explains that: “The encryption and anonymity that a VPN provides helps protect your online activities: sending emails, shopping online, or paying bills.” Another 10 year old view.
The highly trusted Consumer Reports claims that “Just about all security experts agree that using a VPN, or virtual private network, when you’re accessing the internet via computer or phone is a good idea. In particular, a VPN is one of the easiest ways to avoid getting hacked while you’re taking advantage of the free WiFi at an airport or library.” (This is also a false statement. Additionally, saying “Just about all security experts agree” reminds me of “More doctors smoke Camels.”)
An Attorney with the Federal Trade Commission discussing VPNs asserts that: “Public networks are not very secure – or, well, private – which makes it easy for others to intercept your data.” This was once very true. But not quite right anymore.
What I Say About VPNs:
You do not need to use a VPN if you are just trying to secure your personal Internet communications. If you have a well patched operating system and up to date applications, they already establish encrypted communications. Do to changes in standards, this is just the way the Internet and computers work now.
VPN companies would gladly sell you a VPN even if you don’t need one, but that may well just introduce more risk. And it does so while slowing your Internet connection and costing you money.
How Things Used To Be:
A decade ago having a VPN for your personal use was good advice. A savvy technologist could join a public WiFi network and capture packets and read information from other users, including logins, passwords, or even financial information, depending on what people were doing on the WiFi. Soon as a way of showing how this could be done was coded into a browser plugin called FireSheep. The author of this plugin, Eric Butler, did a great service for WiFi security. By showing these vulnerabilities he motivated significant changes.
Other attacks possible in the old days included ways to trick your browser into thinking an attacker is the ultimate destination. The attacker sits in the middle of comms between the user and the ultimate destination and breaks the encryption and replaces it with his own. This is a “man-in-the-middle” attack.
What Has Changed:
In part due to problems of unencrypted traffic and man-in-the-middle attacks, the technology of the Internet and devices and applications have changed pretty significantly. Changes in the way the Internet and our systems work include:
- Massive (successful) investments in security from Apple, Microsoft, and Google. Zero day vulnerabilities and attacks happen, of course but the OSs and applications provided by these firms are much stronger than they have ever been, and the applications warn and stop browsing if attacks like the infamous man-in-the-middle (MITM) are tried.
- Massive engineering of applications used to access the Internet, including web browsers and email applications and all mobile apps to use secure communications.
- A massive move towards encryption of web traffic (HTTPS). All the top websites encrypt all their traffic, not just the login pages like many did 10 years ago.
- The invention of new web technologies, including a new method designed to defeat man-in-the-middle attacks and cookie hijacking. Chief among these protocols is HTTP Strict Transport Security (HSTS).
- Improvements to DNS security standards have also been made, including a protocol called DNS over HTTPS (DoH). This increases security and privacy by making it harder to know what websites a users is looking at and making it harder to manipulate DNS.
- Free certificates from EFF’s Let’s Encrypt project, and helpful tools like HTTPS Everywhere (highly recommended).
So, today Almost all web traffic is now encrypted. And if an attacker tries a man in the middle attack against your web browsing session you will get a warning and the comms will stop. The warning varies from Chrome to Safari to FireFox but all now prevent this type of attack by checking to see if the certificate that set up the HTTPs encryption matches the correct version maintained in trusted stores online.
What Will You See When Attacked:
Here is what you will see if an attacker is on your public WiFi and tries a Man in the Middle Attack:

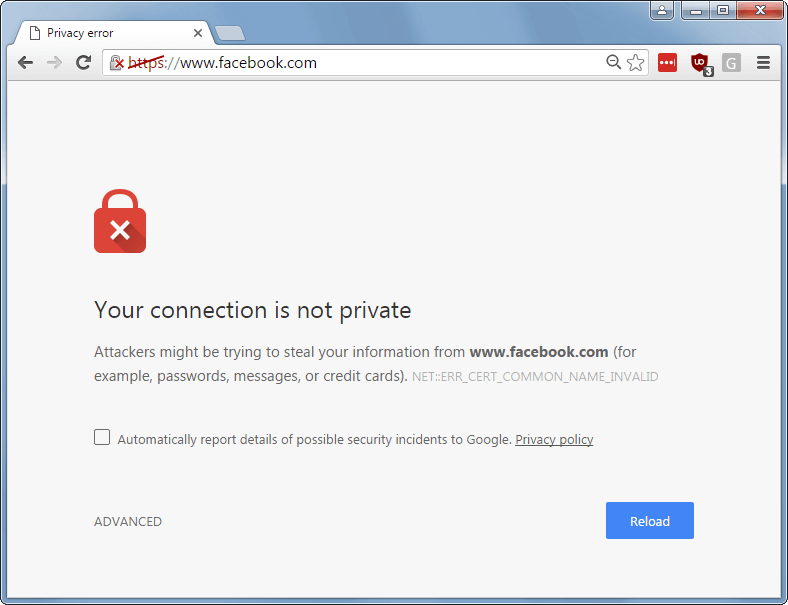
Other Risks With VPNs:
VPNs come with their own risk. There are risks that the VPN company you have picked are not protecting your traffic the way the promised. There are risks that they are logging your info in ways they claim they are not. If you think you are using a VPN to protect yourself from government surveillance, they may actually be making it easier on the government to surveil you. (the EFF provides many great references on some of the issues with VPNs, including here and here).
Nothing is ever perfectly safe (this is about managing risk). But since modern applications set up encrypted channels already, we are at the point where personal VPNs do not seem to add anything that reduces real risk.
When Might You Need A VPN?
As previously mentioned, there are reasons for companies to require a VPN for remote employees. This type of VPN can be used to help companies ensure governance over their data and ensure only authorized users are accessing corporate resources. These also help companies that want to search traffic for malicious code. This corporate VPN needs to be managed and updated of course (see recent CISA statement of corporate VPN vulnerabilities being exploited during the Coronavirus crisis). But in general it can be very smart for a corporation to use this method for access to corporate resources. There are new changes in the offing here too, and VPNs are not the answer to every corporate need (corporate technologists should be closely tracking developments in the software defined perimeter and zero trust worlds, including Google’s Beyond Corp approach).
Many people recommend that journalists and activists and others operating overseas use a VPN, and there may be good reason to do this if operating in a hostile nation. However, the threat model there is very different. And in many cases, using a VPN there will just give a false sense of security. The hostile nation may well be reading all the VPN traffic and logs anyway. People in these situations need far more security than a VPN (including secure messaging systems).
Some people use VPNs so they can pretend to be using the Internet from a certain geography. This is certainly a good use case if you want to do that. But this does not add security.
But I have not seen any argument by a technologist familiar with how the Internet works today that says paying for a personal VPN makes sense for the average user or small business. It does nothing to improve your security or reduce risks in any meaningful way. In fact, it may actually introduce new risks.
Concluding Thoughts:
How could it be that so many security professionals are out there right now advising people at home or small businesses to use a VPN? I can only imagine they have not kept up with how the architecture around them has been changing. And of course no VPN company is going to say they are not needed anymore. But the biggest reason is probably the same reason doctors promoted tobacco or we all thought sugar was ok. It is a bias towards the status quo by people who have not wanted to learn how the Internet has changed.
There are certainly many other important things to do to reduce risk. Chief among those things is using an up to date OS and up to date applications (see this list of tips to reduce personal risk and this list to reduce business risk).
And one final point: If the Chinese Ministry of State Security (MSS) or Russia’s Foreign Intelligence Service (SVR) wants to mount an effort against your Internet use, you have a different threat profile than most of us. But if you think a VPN will slow them down you are fooling yourself. If you need to mount a defense against them let’s talk, we can help, but a VPN is not the thing that will save you from them.