The 11 May 2017 Presidential Executive Order on Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure is notable for several reasons. The order is significant as it discusses improvements to the federal government’s (and the nation’s) digital infrastructure, protection of the power grid, replacement of antiquated IT systems, and protection against cyber threats. It also makes it clear that government leadership is accountable for cyber security. Agency heads can no longer delegate responsibility for cybersecurity to their IT staffs. Risk management of assets is now a part of their mission and must be administered with resources (time, budget, and people) to accomplish this.
Many of us in the cybersecurity community see this order as a positive step. Cybersecurity has always been a leadership issue, but something about human nature has made it incredibly hard for many leaders to get that. This has resulted in an observable phenomenon we call “cyber threat amnesia“, where leaders of organizations forget about the cyber threat as soon as the last problem was handled. As evidence that this phenomenon is part of our nature, we have also long documented a problem the community has in considering every new major attack a “wake-up call“.
We have conducted cybersecurity assessments of firms across multiple sectors of the economy and the government, and have found one key factor is the most important to assess in any organization: If the leader is aware that reducing digital risk is not just an IT function then there is hope. If the leader does not understand this point then educating that leader becomes the priority.
This brings us back to the cybersecurity executive order. We know for a fact that more leaders today are aware of cyber threats and know they must be treated seriously. But by underscoring that agency heads and cabinet department officials are responsible the executive order makes it clear that leaders must lead, and that is very good.
Another thing we really like about the executive order is the requirement that agency heads leverage the NIST Cybersecurity Framework. We have seen first hand how use of this framework can help organizations form a comprehensive look at their policies, process and technology. One of the benefits of the NIST Cybersecurity Framework is it’s language and approach form a taxonomy of common terms that can greatly help in communication around cybersecurity.
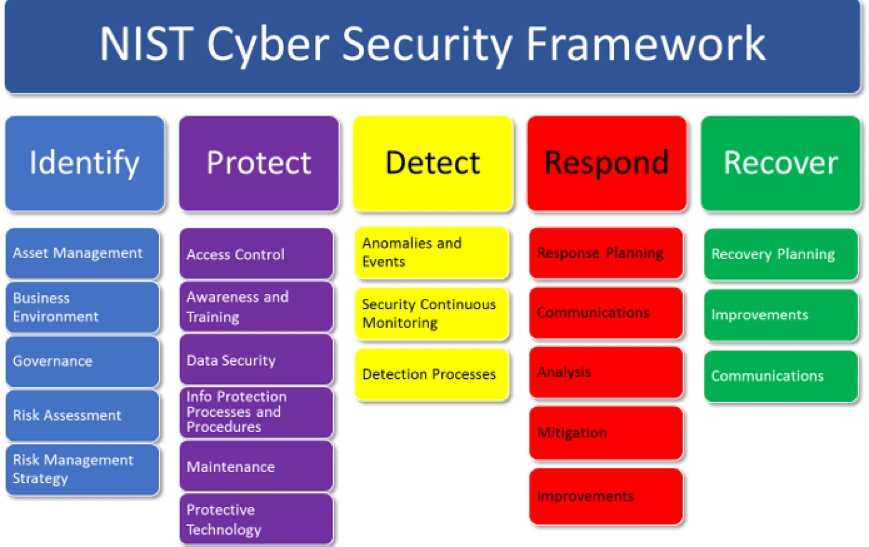
As agency heads move to leverage the NIST Cybersecurity Framework, we urge all to keep in mind that it does NOT adequately address a key component of cyber risk mitigation: the use of external insights to optimize defense. Most in the community are calling this cyber threat intelligence. But what we are really talking about is how to get information from outside the organization that can help defend the organization. This includes subjects like learning what adversaries are doing (so you can optimize defenses against them), learning what your attack surface looks like (so you can spot vulnerabilities and reduce them) or learning successful defense lessons from others in the community.
There are many best practices and solutions that can help address these gaps. One free to use solution in use across government today is the investigative toolset called PassiveTotal by RiskIQ. PassiveTotal makes it easy to discover and proactively block malicious infrastructure and provides analysts with a single view into the data they need for discovering what adversaries are doing.
Other references we recommend for agencies moving out on implementing the executive order include:
- The Cyber Threat: A book providing focused insights on cyber threat intelligence and how to establish an efficient mechanism to get the right information to the right user.
- To learn more see the CTOvision Solutions Directory: RiskIQ
- The Dali Lama As A Business Strategist: His words underscore the need for informed action
- Don’t Buy A Samsung Smart TV Till You Understand The Threat To Your Business And Personal Information