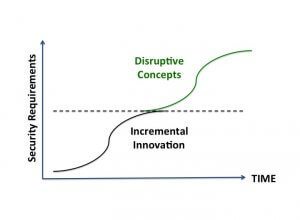
Security professionals by their nature are risk averse. Thus it’s no surprise that the security industry is defined by incremental innovation. Start with something that works and make it better. Unfortunately “innovative security” strategy is leading to an increase in cyber security failures.
Increased spending and increased cyber failures now characterize the security industry. Gartner forecasts that security spend will be on the order of $100 Billion for 2016 yet breaches are occurring with greater frequency than ever before. This is occurring because the existing security architectures have reached their performance envelope.
Organizations are more complex than the assumptions that define current security product design. Incremental innovation no longer works and the security industry requires a disruptive shift to keep pace with organizational needs.
The history of the technology business is defined by systems hitting a wall and then being replaced. For example aviation started with lighter-than-air craft (i.e. balloons) that got replaced by propeller planes that in turn got replaced by jets. Like balloons being blown by the wind in the wrong direction, current security solutions just don’t let organizations go where they want.
In a world defined by mobile users, non-employees and diverse infrastructure having twenty to fifty different point products doesn’t work as there is no way to integrate their logic. To protect today’s organization we need a new security architecture based on inter-locking components:
- Identity-based access control that protects data center and cloud assets
- Policy-based data encryption that is tied to the access control system
- Data center and cloud partitioning solutions that create compute containers
- Identity services that dynamically determine policy based on location and device
- Mobile compute devices supporting partitioned, secure code execution
Each security component is designed to support the other four requiring cyber attackers to break all five to breach an organization. More importantly, as new devices, users or apps go online, the entire system is aware of the changes – making it extremely difficult for cyber attackers to find a weakness in the system.
The strong bias in the security industry against disruptive ideas has become a barrier to move forward. It’s time for security professionals to focus on strategies to reduce cyber risk than solutions that are less risky.
Also see: