We have previously written about Recorded Future, a fast moving startup delivering predictive signals from the noise of the web. Recorded Future provides a blog that captures several exemplars of their capability and its applicability in many mission areas. One mission area of particular interest in the use of Recorded Future for Cyber Security missions.
Today Recorded Future posted another informative piece on this theme titled: “Improving Cyber Threat and Vulnerability Assessment with Web Intelligence”
Here is an excerpt:
The concept behind Recorded Future is simple to understand (though difficult to implement) and is certainly not based on psychic visions. What the company does is gather content from the open web, filter it, analyze it, and generate predictive signals based on the refined information. Simply put, it is organizing the open source information from the web. For example, it may be useful to understand the social media discussions from a particular area when forecasting a regional election.
Recorded Future for Cyber Security
This kind of technology is very helpful in domains that require attention to and analysis of what is being discussed on the web and how information is linked. From the cyber security point of view, this technology is useful not only for reconnaissance (first phase of pentesting) on a target but also to learn about cyber attacks in the form of malwares, APTs, DDoS attacks, etc.
Examples
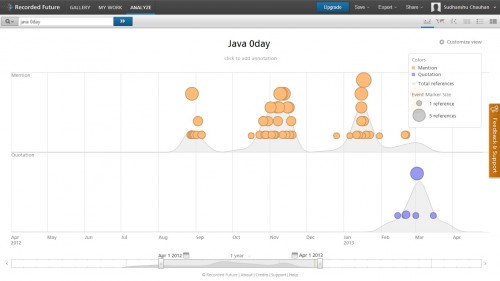
Let’s take the example of Java 0-day vulnerabilities. Figure 1 clearly shows the huge amount of mentions of the topic (Java 0-day) during the past year especially between August 2012 and February 2013. This information could be crucial for any corporation using Java in its product development. Based upon this graph they could issue warnings to their consumers to keep their Java versions updated and incorporate other defense mechanisms to safeguard themselves. Similarly, this information is helpful to end users in understanding the risks that a particular technology poses at any given time.
The post also presents an insightful tree map of Ransomeware and ideas for how to operationalize the information.
The post goes on to offer suggestions to Recorded Future on other sources that analysts need to tap into. Since this blog post was hosted on the Recorded Future site I imagine this means they are going to be working on those suggestions.
Please check the post out here: http://ctolink.us/13xJ20D
Related Posts:
An Introduction to Recorded Future: An ability to leverage the predictive power of the web