Smart Cities will become a full-scale cyber war battleground unless Congress mandates cybersecurity.
The biggest danger in Smart Cities is the assumption that IoT sensors communicating over a 5G fabric to Machine Learning and Blockchain systems will be safe from cyberattacks. To the contrary Smart Cities suffer from all the cyber vulnerabilities we have today (like phishing password attacks, server exploitation and self-propagating malware (especially ransomware)) plus a new generation of attack vectors due to the hyper-connected state of everything.
State-Sponsored Infiltration: We haven’t even built our first Smart City but we’ve already had our first geo-political incident. DHS recently banned Huawei’s 5G equipment when it was discovered that the Chinese government could remotely listen to any communication in the USA. The loss of domestic American telecom manufacturing makes Smart Cities vulnerable to equipment imported from hostile states. In addition to direct infiltration, the global supply chain provides ample opportunity to modify software and slip in via domestic suppliers.
Personal Targeting: Currently there are no guidelines to limit what IoT sensors can see inside your home or on the street. Self-driving cars see and hear everything while moving (even at high speed). Facial recognition software can track you as well as determine your social connections (people you talk and who they talk to). The vast amount of personal data makes personal targeting a reality. Take for example ransom (not ransomware but real ransom) from being locked in your self-driving car or smart elevator until you make a big crypto-currency payment.
Market Theft: One of the highly promoted aspects of a Smart City is a Blockchain-based market to buy and sell items like energy. While Blockchain provides a tamper proof record of a transaction it doesn’t guarantee the input data is valid. For example, one could trick Smart air conditioners that it’s very hot and have them buy expensive power from a high priced supplier. The ability to hijack a market creates many new opportunities to steal money. Subsequently all the business logic and financial systems in a Blockchain-based market require significant protections against tampering.
The Proposal: Smart City Cybersecurity Framework
To address Smart Cities cyber risks we require a new framework to mitigate state-sponsored infiltration, protect personal privacy and enable an efficient market. However Smart Cities are so complex that the conventional compliance model isn’t going to work. We need a new approach that defines clear roles and responsibilities for every vendor and service provider. To start the process, it’s useful to divide a Smart City into the First Mile, Management and Market sections. We can then look at each section to explore their cybersecurity responsibilities.
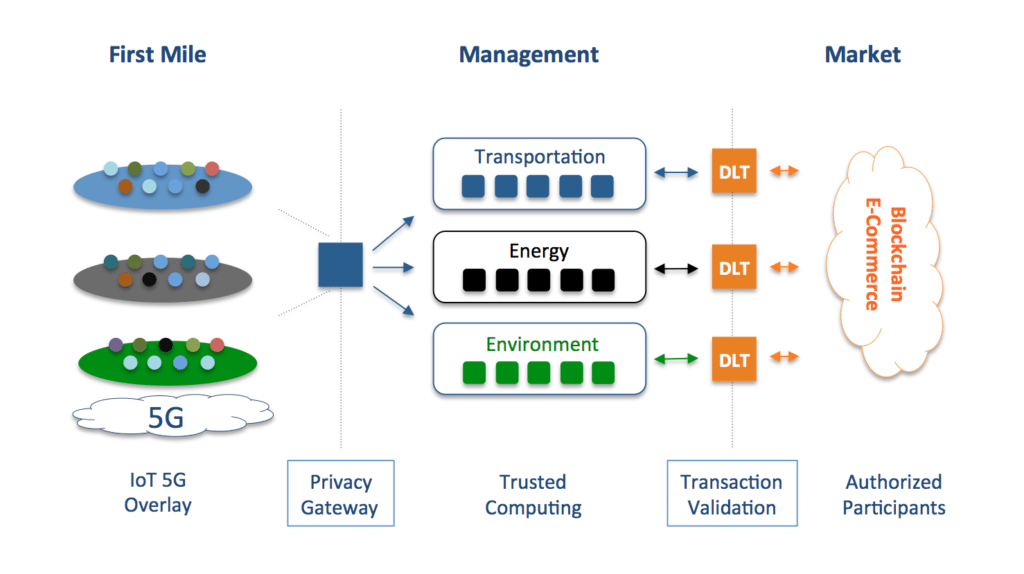
First Mile: The First Mile is plagued with IoT and 5G vulnerabilities. IoT sensors are extremely vulnerable to tampering leading to DDoS and malware attacks on management systems. Additionally the lack of trusted 5G infrastructure opens the door to foreign surveillance. A solution to both problems is to build an IoT overlay network using a Zero Trust Network (ZTN). ZTN’s validate the identity and software of IoT devices before provisioning connectivity. Moreover connectivity would not rely on the 5G network for encryption as the ZTN would utilize its own certificates to establish a mutual TLS VPN.
Privacy Gateway: The First Mile is that is where Smart City citizens are the most vulnerable to personal data mining. Subsequently a Privacy Gateway that strips away Personally Identifiable Information (PII) before data is sent to Management systems is critical. A Privacy Gateway is similar to a GDPR database except that is reads the contents of packet streams and removes facial details (from HD cameras) and human speech (from home appliances) in real time.
Management: Given the mission critical nature of guiding vehicles and power generation systems Management systems should run on a Trusted Computing platform. Software processes like machine learning and administrative control should all run in their own Secure Enclave to mitigate self-propagating malware and inside attacks. Another issue with machine learning systems is their ability to determine data which has been purposely remove. For example traffic systems could easily determine who the owner of a vehicle is and their travel patterns even after the Privacy Gateway removed the driver’s image and license plate from the HD camera feed. Thus all analytics will need to be stored in a separate Secure Enclave the PII stripped off (again).
Data Validation: To ensure that corrupted data does not makes its way into a Blockchain market a Data Validation Gateway is required. This would be similar to the monitoring system stock markets now use to detect unusual trading activity however their logic would have to be expanded to handle the wide array of products and services in a Smart City exchange. Thus homes with Smart Appliances that like to buy expensive services will need to have their activity monitored by a Data Validation Gateway.
Market: Bitcoin made it’s mark as an anonymous cryptocurrency. Unfortunately anonymous trading is not what we want when it comes to managing energy and transportation trading. Thus secure digital wallets with strong authentication (ideally implemented in a Trusted Computing platform) combined with authorized trading limits will be critical for efficient market operation.
Whether we utilize a framework like the one presented or develop a new one, a comprehensive cybersecurity strategy is critical. Congress must mandate a minimum cybersecurity standards for Smart Cities before large scale deployment happens.
Additional Resources:
What You Need To Know About Bitcoin: Including potential new business models to consider
OODAloop nails it again with reporting on Bitcoin price manipulation
From Crowdsourced Militias to Dread Bitcoin Pirates
Today Every Company Buys Electricity, Tomorrow Every Company Will Buy Ethereum
Smart Cities Cybersecurity Challenge
Blockchain Templates: Amazon Making Technology Mainstream
What Executives Should Know About Ethereum
Cryptocurrencies and their promise for enterprise technology professionals
 I can already hear the chuckling. “Cyber warfare? Balanced? And I’d like partisanship in Washington to end, a double date with Mila Kunis and Scarlett Johansson, and some fries with that!” Yes, my desire is utopian, but the fact that I would have to qualify it with a self-deprecating remark suggests the distance that we have yet to travel before we can get more value out of our present conversation on the topic of cyber warfare.
I can already hear the chuckling. “Cyber warfare? Balanced? And I’d like partisanship in Washington to end, a double date with Mila Kunis and Scarlett Johansson, and some fries with that!” Yes, my desire is utopian, but the fact that I would have to qualify it with a self-deprecating remark suggests the distance that we have yet to travel before we can get more value out of our present conversation on the topic of cyber warfare.