Digital Certificates are a foundational building block of the Internet. They are used to verify the identity of e-commerce sites, the authenticity of software and encrypt data. Not surprisingly, cyberattackers try to create fake Certificates or get the Private Keys for real ones to steal data or intercept communications. No one really worried about the Certificates themselves – until now. It seems the random numbers used to generate Certificates sometimes are the same.
To understand the problem it’s useful to take a 30 second tutorial on Digital Certificates. For those of you who might have managed to stay awake during math class you’ll remember that Asymmetric Cryptography utilizes 2 prime numbers to create a Public and Private Key for a Digital Certificate. The Public Key maps an input (that you want to keep secret) to a large number field while the Private Key reverses the transaction. The theory goes that since there’s an infinite set of prime numbers, there’s an infinite set of Public/Private key combinations. To make sure the prime numbers are different a Random Number Generator (RNG) is used. Sounds pretty secure. Infinite is a big number. What could go wrong?
Well the real world is a bit different than math class. It seems the random number generators (RNG) on computer devices really don’t generate an infinite set of primes but rather a bounded set that in turn generates a set of Public/Private Key combinations. This new analysis is a result of the dramatic cost reduction in high performance computing that now enables the simulation of a chip’s RNG function and the Certificates they generate.
From an Internet security perspective, the ability of a cyberattacker to know an organization’s Private Key has huge implications. Attackers can potentially impersonate web sites, intercept secure connections or decrypt any piece of data just by looking at the Public Key. Examples of this attack are not just seen in labs. In one case, for instance, on January 7 2019 the University of California Davis sent an advisory of all students visiting China that their “secure” What’sApp messages were being monitored.
For enterprises that rely on Digital Certificates for their security, which is nearly everyone, it’s important to deploy countermeasure to RNG-based Certificates attacks:
Upgrade Your RNG: Many PKI systems have the ability to connect to an external Random Number Generator or utilize an entropy pool to ensure randomness. If your HSM/Root CA has this capability, it is highly advisable you turn it on. Next you’ll want to purge your network of old Certificates.
Switch to a Virtual HSM: If your existing PKI can’t work with an external RNG or entropy pool then you might consider one of the many cloud-based and software-based HSM solutions. All of the newer software-based PKI solutions support external RNG or entropy inputs. If shopping around, also look for a solution that makes it easy to create and propagate new Certificates – it’ll make your life easier.
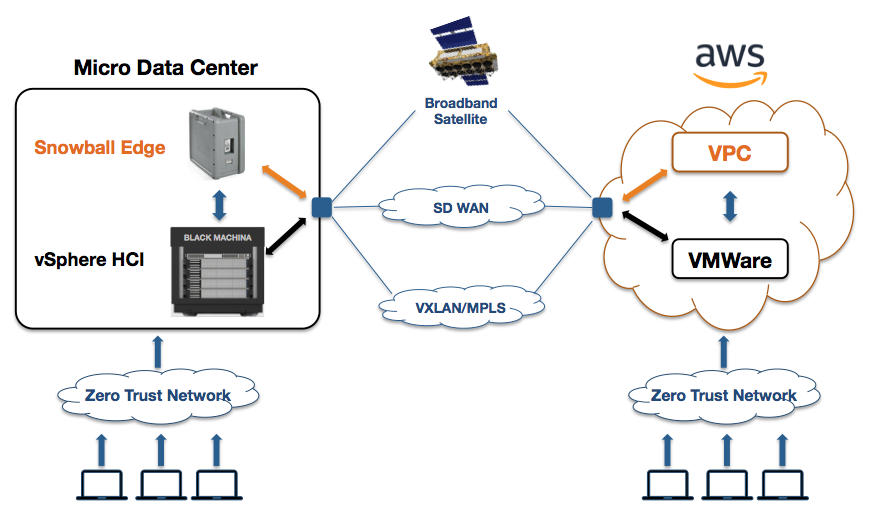
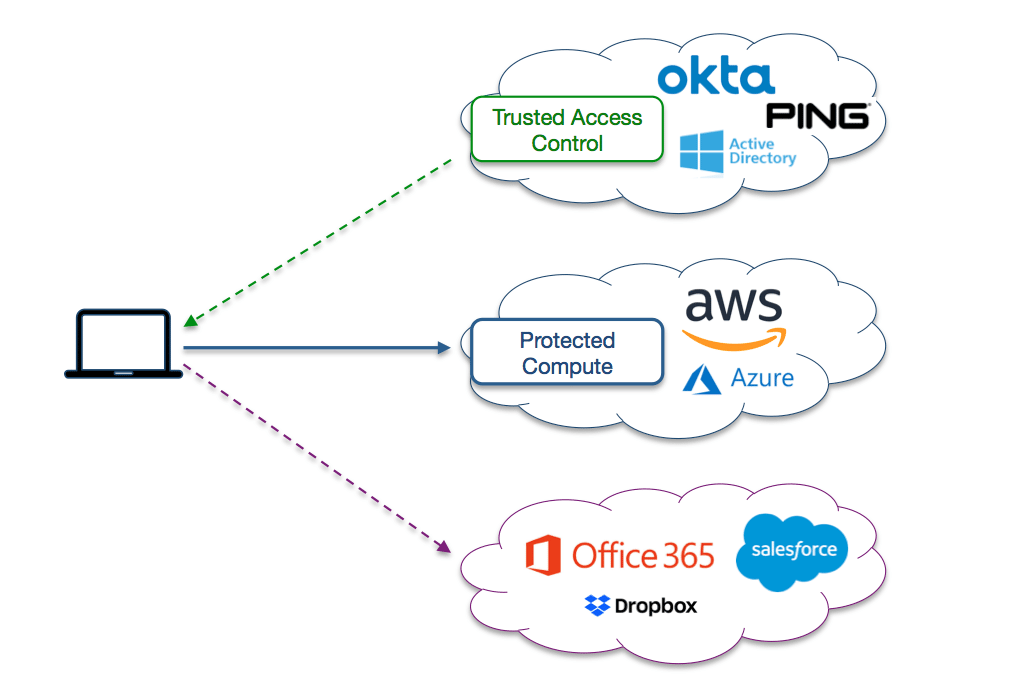
Isolate Mission Critical Apps: In addition to upgrading your Certificates another important countermeasure is isolating high value or mission critical applications from the Internet. Software Defined Perimeter (SDP) is an ideal countermeasure to Certificate attacks as no one except authorized users will even know about the application. SDP can also be used to continuously propagate new Certificates to user devices.
With RSA around the corner, security professionals have a great opportunity for FREE consulting. Ask Certificate and encryption vendors for their countermeasures to existing and emerging Certificate attacks. When visiting a cloud-based SaaS, ask them what countermeasures they have implemented to ensure their Certificates don’t get attacked. Be aware; be proactive as this threat is real.
Related Posts:
An Introduction to Risk Analysis
Connected Devices, Remote Security: Data Encryption and Security in the Cloud
Naturally Better Security: Leveraging the power of nature to enhance Internet security