For the last decade enterprise architects have all known the importance of engineering continuous connectivity to cloud services. If you want to use the cloud you have to have a path to it.
For parts of the enterprise who may operate at the edge, where connectivity can be an issue, it has been hard to design solutions leveraging public clouds. Depending on the organization, edge users might have some mix of public cloud, private cloud, datacenter access and local compute, all complex and hardly optimized at all.
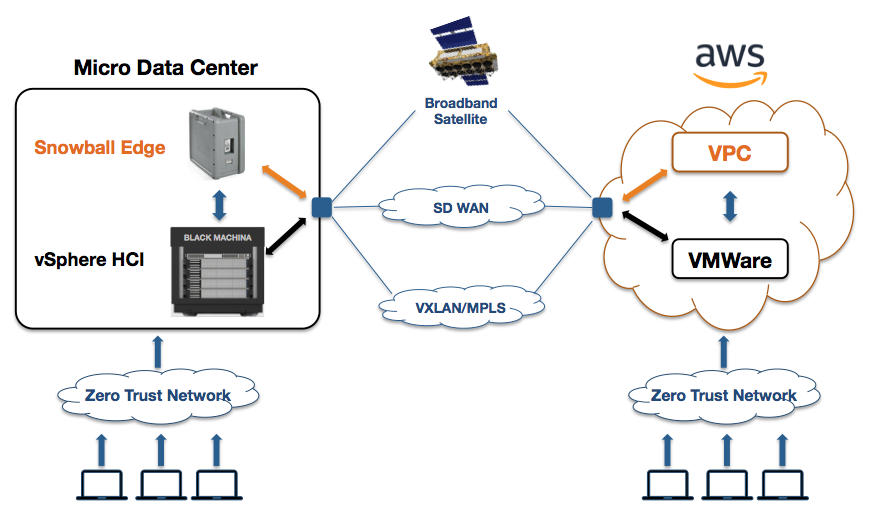
The continuously evolving capabilities of Amazon’s Snowball devices are changing these old approaches. Initially the Snowball was a great way to move data from enterprises to the Amazon cloud. Load the data on the device and ship it. This is still a key use case. But newer versions of the device (the Snowball Edge) included enough processing power to do compute on the edge, meaning many analytics could be done on data before moving it to the cloud. The device soon evolved to be a mini-Amazon instance that can be used in disconnected locations. Now Amazon has just announced a new version of AWS Snowball Edge. The features of this device are giving enterprise architects much more flexibility in meeting the needs of users for high end processing anywhere the data is.
(A picture of the Snowball at the DoDIIS conference is below)

A key thing that enterprises can do with this new version: The extra CPUs and GPUs now enable on site, local Machine Learning (ML) and local analytics. Yep, these things are AI in a box. And this includes very high end advanced analytics like image processing and full motion video analysis.
Here are the details from Amazon:
Soon, you will be able to use AWS Snowball Edge Compute Optimized for edge processing use cases that require additional computing power in remote, disconnected or austere environments. The new configuration comes with 52 vCPUs and an optional GPU so you can perform real-time full-motion video analysis and advanced analytics before transferring the data back to Amazon S3.
Snowball Edge Compute Optimized features more powerful Amazon EC2 instances and 7.68 TB of NVMe SSD to run powerful applications in locations with little or no connectivity. It also provides storage capacity of 42 TB to transfer the processed data into AWS for further analysis or archival. With today’s announcement, customers can choose between a storage optimized and a compute optimized option to process and transfer any sized data volumes into AWS. You can also now cluster the Storage Optimized and Compute Optimized Snowball Edge together to have durable storage for data collection along with powerful compute and high-speed storage for processing in edge locations.
Just to make sure you caught that, you can do full motion video analysis with these things… as well as most any other analytical workload… on the edge. Pretty cool.
Also see:
- Pause And Take Note Of The Remarkable Engineering In AWS Snowball and AWS Snowball Edge
- AWS Snowball Edge And Hyper Converged Infrastructure Will Revolutionize Global Enterprises
- Amazon AWS: Dominating In Cloudcomputing, Data Analytics, Artificial Intelligence and IoT
- Google: Innovating in AI but can they catch up with cloud leaders?
- IBM: Technology for both enterprises and the startup world
- Apple: Increasingly an enterprise IT company
- VMware: A Tech Titan And Leader In Cloud Infrastructure and Digital Transformation
 The DoDIIS Conference is almost upon us. August 12-15, 2018, members of the defense intelligence community will gather in Omaha for several days to listen to the latest in mission needs and requirements from key government leaders and to witness demonstrations of cutting edge IT on a very well attended expo floor.
The DoDIIS Conference is almost upon us. August 12-15, 2018, members of the defense intelligence community will gather in Omaha for several days to listen to the latest in mission needs and requirements from key government leaders and to witness demonstrations of cutting edge IT on a very well attended expo floor.